Zero Trust Security: A Comprehensive Guide for Businesses
Discover how Zero Trust Security can safeguard your business. Learn the principles, benefits, and steps for implementing this critical cybersecurity strategy.
In today’s fast-paced world of cybersecurity, the old security models just can’t keep up with the ever-evolving and increasingly clever cyber threats we face. The once-reliable principle of "Trust, but Verify" has become a relic, especially with the rise of advanced persistent threats (APTs), insider attacks and the growing number of remote workers. Because of this, many companies are now embracing Zero Trust Security (ZTS) to strengthen their defenses.
Zero Trust is a cybersecurity strategy that operates on the premise that no user, device or network should be trusted by default, whether they’re inside or outside the corporate environment. Instead of relying on conventional perimeter defenses, Zero Trust prioritizes strict identity verification, limited access rights, and continuous monitoring.
In this guide, we’ll dive into what Zero Trust Security is all about, its essential components, the benefits it offers, and how businesses can effectively implement it.
What is Zero Trust Security?
Zero Trust Security is based on a straightforward but effective principle: "never trust, always verify". Unlike traditional security models that assume users and devices within the corporate network are trustworthy, Zero Trust treats every access attempt whether it’s from an internal employee or an external threat as untrusted.
Here’s what that means:
- Verification for every access request: Every user and device must be verified before they can access any resources.
- Least-Privilege Access: It means that users and devices receive only the minimal level of access necessary to complete their tasks.
- Continuous Monitoring and Logging: The network is under constant surveillance to spot any unusual behavior that might signal a potential breach.
Zero Trust understands that threats can emerge from both outside and inside the organization, which is why it adheres to the “never trust, always verify” approach to safeguard resources throughout the entire network.
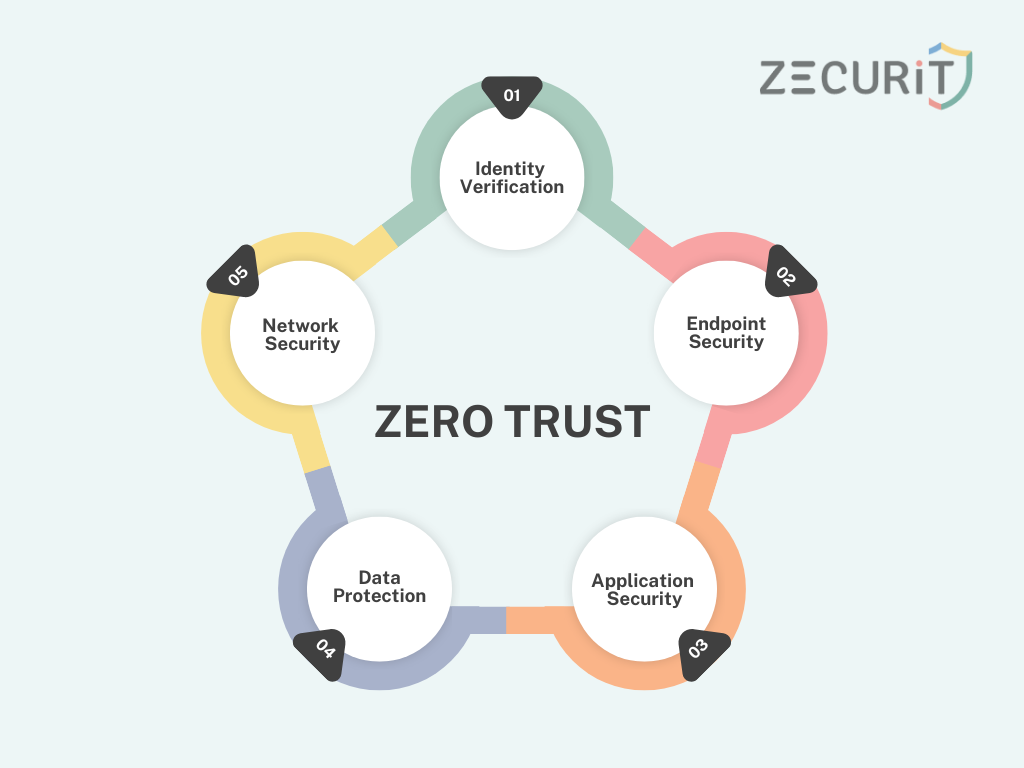
Key Components of Zero Trust Security
Zero Trust isn’t just a cookie-cutter approach, it’s a detailed strategy that weaves together several essential elements. Let’s dive into the key components that make up Zero Trust:
- Identity and Access Management (IAM)
- Multi-Factor Authentication (MFA): A crucial part of Zero Trust is verifying that users are who they claim to be. This is where multi-factor authentication (MFA) comes into play, requiring users to provide two or more forms of identification, something they know (like a password), something they have (like a smartphone), or something they are (like biometric data).
- Identity Federation: This enables users to access multiple systems with a single set of login credentials. It minimizes the risk of credential theft while keeping centralized control intact.
- Least-Privilege Access
- Zero Trust employs role-based access control (RBAC) or attribute-based access control (ABAC) to ensure that users, devices or applications only get the minimum access they need to do their jobs.
- For instance, an HR employee should only have access to HR-related data, not finance or IT systems, even if they’re on the company network.
- Micro-Segmentation
- Micro-segmentation is all about breaking a network into smaller, isolated segments, each with its own security measures. This approach helps contain potential damage from a breach, as a hacker who gets into one segment can’t easily spread throughout the entire network.
- For example, critical databases might be kept separate from general office networks to block unauthorized access, even from users within the organization.
- Network Traffic Encryption
- Encryption guarantees that data transmitted between devices or users is safeguarded against interception and alteration. Within a Zero Trust framework, all network traffic both internal and external is encrypted by default
- Tools like VPNs and SSL/TLS encryption are essential for ensuring that sensitive information stays secure, even when accessed from remote locations.
- Endpoint Security
- Every device that connects to the network can be a potential entry point for attacks. Zero Trust takes this seriously by ensuring that each endpoint be it a laptop, smartphone or IoT gadget is constantly monitored for security vulnerabilities, updated with patches and compliant with security policies before it can access any network resources.
- Endpoint Detection and Response (EDR) tools are invaluable in spotting malicious activities on these endpoints and can react to potential threats in real-time.
- Continuous Monitoring and Analytics
- Zero Trust places a strong emphasis on the ongoing monitoring of all network activities. By leveraging advanced analytics and machine learning, security tools can identify unusual behaviors or anomalies, such as login attempts from unexpected locations or at odd times, which could signal a possible breach.
- Security Information and Event Management (SIEM) systems play a key role by collecting and analyzing logs from across the organization’s network, giving a comprehensive view of the overall security posture.
Benefits of Zero Trust Security for Businesses
Embracing a Zero Trust model brings a wealth of benefits to organizations, especially as cyber threats grow more complex and widespread:
- Enhanced Security Posture
- Zero Trust operates on the principle that no device or user can be automatically trusted. This approach significantly reduces the risk of lateral movement, making it tougher for attackers to exploit network trust and elevate their privileges once they breach the system.
- With robust identity and access management paired with ongoing monitoring, it becomes increasingly challenging for intruders to sneak into critical systems or sensitive data unnoticed.
- Addressing Insider Threats
- Conventional security models often overlook the potential dangers posed by insider threats. Zero Trust recognizes that risks can originate from within the organization as well as from outside, making it more adept at identifying and addressing both types of threats.
- Enhanced Compliance
- Zero Trust can assist organizations in adhering to regulatory standards like GDPR, HIPAA, and PCI DSS, which demand stringent data access controls and continuous oversight.
- By continuously auditing and logging user activities, businesses can effectively demonstrate compliance with data protection and privacy regulations.
- Better Support for Remote Work
- With remote work becoming the norm, Zero Trust is particularly effective in safeguarding remote employees who access company resources from outside the traditional office environment. Unlike standard VPNs that often depend on perimeter-based trust, Zero Trust ensures that remote users are consistently authenticated and authorized for access.
- Reduced Attack Surface
- Techniques like micro-segmentation, least privilege access and endpoint security all contribute to shrinking an organization’s attack surface. By restricting access and isolating critical systems, Zero Trust makes it significantly more difficult for attackers to identify vulnerabilities.
Steps for Implementing Zero Trust Security
Implementing Zero Trust Security can seem daunting since it requires a complete rethinking of traditional security models within an organization. But with some thoughtful planning and execution, businesses can effectively embrace Zero Trust principles.
Here is a simple guide to assist you in implementing Zero Trust:
- Assess Current Security Posture
- Start by conducting a comprehensive audit of your existing security measures, policies, and network setup. Look for vulnerabilities, gaps and areas where Zero Trust can enhance your security.
- Define the Protect Surface
- Identify the critical assets that require the highest level of protection, such as sensitive data, applications, and systems. These assets make up your "protect surface," and your Zero Trust strategy should focus on securing them.
- Implement Strong Identity and Access Controls
- Utilize robust identity and access management (IAM) solutions, including multi-factor authentication (MFA) and single sign-on (SSO). Make sure that users, devices, and applications are continuously verified before they can access any resources.
- Enforce Least-Privilege Access
- Use role-based or attribute-based access control to ensure that least-privilege access is enforced throughout the organization. Regularly review and update access permissions to guarantee that users only have access to the resources they truly need.
- Deploy Micro-Segmentation
- Break your network into isolated segments to contain potential breaches and restrict attackers' ability to move laterally within the network.
- Enable Continuous Monitoring and Incident Response
- Set up continuous monitoring tools like SIEM, EDR, and NDR to detect and respond to threats in real-time. Develop an incident response plan to swiftly address any security incidents that arise.
- Educate and Train Employees
- Zero Trust isn't just about the tech; it's about fostering a culture of security. It's crucial to educate your team on why security matters and to train them to spot phishing attempts, create strong passwords, and adhere to company security protocols.
- Iterate and Improve
- Implementing Zero Trust is an ongoing process, not a one-time effort. Keep a close eye on how well your security measures are working, pinpoint areas that need enhancement, and stay agile in the face of new threats.
Conclusion
Zero Trust Security presents a contemporary and effective strategy for tackling cybersecurity challenges in our increasingly intricate threat landscape. By removing blanket trust and verifying every user, device and connection, organizations can significantly lower the chances of data breaches, insider threats and sophisticated cyberattacks.
Although transitioning to a Zero Trust model can be somewhat complex, the benefits such as improved security, regulatory compliance and a reduced attack surface, make it a crucial strategy for any organization committed to safeguarding its digital assets. By rolling out Zero Trust in a structured way, businesses can create a strong, adaptable security framework that evolves alongside the ever-changing cyber threat landscape.
Frequently asked questions:
-
What is Zero Trust Security?
Zero Trust Security is a cybersecurity model that assumes no device or user is inherently trusted, whether inside or outside the network. Every access request is verified, ensuring robust security.
-
Why is Zero Trust important for businesses?
Zero Trust is vital because traditional security models are insufficient in today's cyber threat landscape. It helps prevent insider and external attacks by continuously verifying users and devices.
-
What are the core principles of Zero Trust?
The core principles of Zero Trust include:
- Never trust, always verify
- Enforce least-privilege access
- Continuously monitor and log network activity
- Isolate critical assets through micro-segmentation
-
How does Zero Trust differ from traditional security models?
How does Zero Trust differ from traditional security models?
-
How can businesses implement Zero Trust Security?
Businesses can implement Zero Trust by focusing on:
- Strong identity and access management
- Micro-segmentation of their network
- Continuous monitoring for anomalies
- Enforcing least-privilege access policies
-
Is Zero Trust only for large enterprises?
No, Zero Trust can be implemented by businesses of all sizes. While larger organizations may need more complex solutions, small to medium businesses can still leverage simplified Zero Trust frameworks with tools tailored to their needs.
-
What are the benefits of Zero Trust for remote workforces?
Zero Trust is particularly effective for remote workforces by ensuring that all users and devices, regardless of location, are authenticated and granted the minimum necessary access, thus securing corporate resources from potential threats.
-
Does Zero Trust mean I need to overhaul my existing security infrastructure?
Not necessarily. While Zero Trust may require integrating new tools and technologies, it can often be implemented in stages, building on your existing security framework without requiring a complete overhaul.