Compare EDR, MDR, and XDR capabilities to make informed decisions on advanced threat detection, response, and managed defense.
In today’s dynamic cybersecurity landscape, organizations face an ever-evolving array of threats, making robust detection and response strategies essential. Among the most widely discussed solutions are Endpoint Detection and Response (EDR), Managed Detection and Response (MDR), and Extended Detection and Response (XDR). Understanding the distinctions among these options is crucial for businesses seeking to strengthen their security posture effectively.
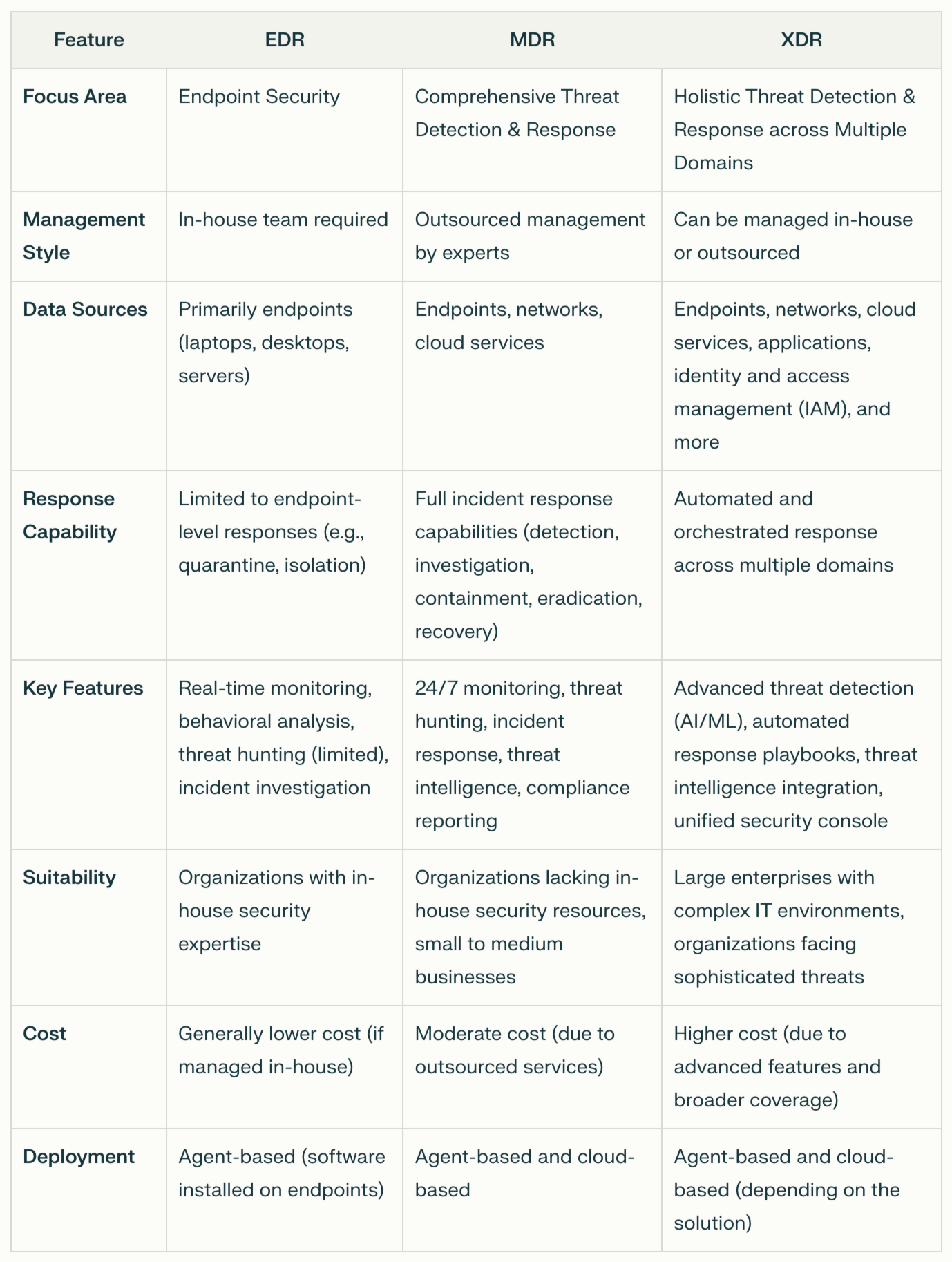
Endpoint Detection and Response (EDR) focuses on monitoring and securing endpoint devices within a network. These include laptops, desktops, and servers, devices often targeted by cyberattacks. EDR solutions use software agents installed on these endpoints to continuously gather and analyze data in real-time. This allows for the rapid detection of suspicious activities and potential threats.
EDR is best suited for organizations with skilled in-house security teams capable of managing the tools and responding to threats effectively.
Managed Detection and Response (MDR) builds upon the capabilities of EDR by incorporating outsourced security services. MDR combines advanced technology with human expertise to deliver 24/7 monitoring and response capabilities. This solution is particularly beneficial for organizations that lack the resources or expertise to manage security operations internally.
MDR is an excellent choice for smaller organizations or those without dedicated security teams.
Extended Detection and Response (XDR) is an evolution of EDR, offering broader visibility by integrating data from multiple sources beyond just endpoints. It consolidates information from networks, cloud services, and other security tools to provide a holistic view of an organization’s security posture.
XDR is ideal for organizations with complex IT environments facing advanced and multi-faceted cyber threats.
When deciding between EDR, MDR, and XDR, organizations should evaluate several factors:
Choosing the right vendor is crucial for effective threat protection. Here are some of the leading players:
Please check out: Top EDR tools on the market.
Choosing the right vendor depends on your specific needs and budget. Consider factors such as the level of threat protection required, the desired level of automation, and the need for managed services. It's recommended to evaluate multiple vendors and conduct thorough proof-of-concept tests before making a decision.
In summary, EDR, MDR, and XDR each play unique roles in an organization’s cybersecurity strategy. By understanding their differences in focus areas, management styles, data sources, and response capabilities, businesses can make informed decisions tailored to their specific requirements. Ultimately, the choice will depend on factors such as organizational size, in-house expertise, threat landscape complexity, and budget. Selecting the right solution ensures a stronger and more resilient security posture in an ever-changing cyber threat environment.
EDR focuses on securing endpoint devices like laptops and servers, requiring an in-house security team to manage alerts and responses.
MDR combines EDR technology with outsourced 24/7 monitoring and response services, making it ideal for organizations without in-house expertise.
XDR extends beyond endpoints, integrating data from networks, cloud environments, and other sources to provide a holistic security view, suitable for complex IT environments.
MDR is often the most cost-effective choice for small organizations. It provides expert management, 24/7 monitoring, and comprehensive threat response without requiring a dedicated in-house security team.
XDR improves threat detection by correlating data from multiple sources, such as endpoints, networks, and cloud services, offering a unified view. This broader integration helps identify complex, multi-faceted threats that might go unnoticed with endpoint-focused EDR solutions.
Yes, EDR can be a standalone solution, but it requires a skilled in-house security team to manage alerts, analyze threats, and respond effectively. Organizations without sufficient expertise may struggle to utilize EDR to its full potential.
Key Factors to Consider
FEATURES
EXPLORE IT Asset Management