What is Patch Management ?
A Complete Guide to Secure Your Business
This guide provides a comprehensive overview of patch management, explaining its importance and how to implement it effectively to secure your business.
What is Patch Management?
Patch management is the process of identifying, testing, deploying, and tracking software updates (vendor-issued patches) for software and devices. This helps fix security vulnerabilities and ensures everything runs smoothly.
Hackers are taking advantage of unpatched vulnerabilities as their main way to launch attacks, which really emphasizes how important it is to keep up with security updates. If organizations neglect to apply these updates, they leave themselves open to serious security risks.
The Importance of Patch Management
In our fast-paced digital landscape, ignoring patch management can lead to serious repercussions for any organization. It’s not just a simple IT chore anymore; it’s a vital part of keeping your security intact. Let’s dive into the reasons why this is so important:
1. Enhanced Security:
- Mitigating Exploits: Cybercriminals are always on the lookout for software vulnerabilities. That's where patches come in, they're created to fix these security issues, especially those that malware like ransomware, viruses, and Trojans take advantage of. By applying these patches quickly, you can really shrink the chances of security attack and keep hackers from getting unauthorized access to your systems and data.
- Blocking Ransomware: Ransomware attacks frequently take advantage of vulnerabilities that are already known. By applying patches promptly, you can effectively stop many of these attacks in their tracks, safeguarding your data from being encrypted and avoiding those ransom demands.
2. Improved System Stability and Reliability:
- Reduced Crashes and Errors: Patches usually come with bug fixes and performance improvements. By applying these updates, you can reduce the chances of system crashes, freezes, and other unexpected error, resulting in a smoother and more dependable experience.
- Enhanced Performance: Some patches are specifically designed to improve system performance, such as optimizing resource utilization and speeding up processes.
3. Increased Productivity:
- Minimized Downtime: Unpatched systems are more prone to failures and downtime. By keeping systems updated, you minimize disruptions to business operations, ensuring employees can remain productive and meet deadlines.
- Improved User Experience: Stable and reliable systems contribute to a better user experience, leading to increased employee satisfaction and productivity.
4. Reduced Costs:
- Preventing Data Breaches: Data breaches resulting from unpatched vulnerabilities can be incredibly costly, involving expenses for data recovery, legal fees, and reputational damage. Proactive patch management helps prevent these costly incidents.
- Minimizing System Failures: System failures caused by unpatched software can lead to significant downtime and revenue loss. Patching helps prevent these costly outages.
5. Compliance with Regulations:
- Meeting Industry Standards: Many industries have regulations and compliance standards that require organizations to maintain secure systems. Effective patch management demonstrates compliance with these standards, such as HIPAA, PCI DSS, and SOX.
- Avoiding Penalties: Non-compliance with these regulations can result in hefty fines and legal repercussions. Patch management helps organizations avoid these penalties.
6. Maintaining Brand Reputation:
- Protecting Customer Trust: Data breaches and security incidents can severely damage an organization's reputation, eroding customer trust. By prioritizing patch management, you demonstrate a commitment to data security and protect your brand image.
Patch management is not just about keeping software updated; it's a fundamental aspect of cybersecurity and overall IT health. By prioritizing this critical process, organizations can significantly enhance their security posture, improve system stability, boost productivity, reduce costs, and maintain compliance with industry regulations.
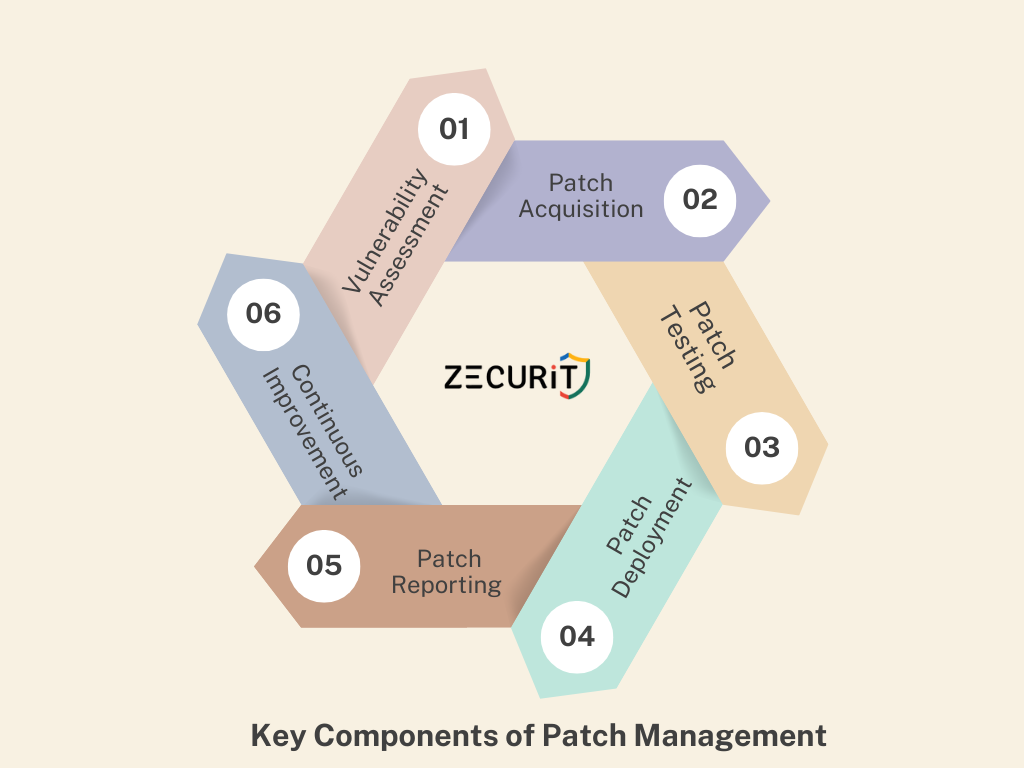
Key Components of Patch Management
Patch management is a multi-faceted process that goes beyond just downloading and installing updates. Let’s take a closer look at its essential components:
1. Vulnerability Assessment:
- Discovery and Identification: The process involves with identifying all devices and software within your environment. This includes servers, workstations, mobile devices, and applications.
- Vulnerability Scanning: Regular vulnerability scans are crucial. These scans use automated tools to identify known security weaknesses in your systems and software.
- Prioritization: Not all vulnerabilities are created equal. Prioritize patches based on factors like:
- Severity: Critical vulnerabilities (e.g., those actively exploited by attackers) should be addressed immediately.
- Impact: Consider the potential impact of a vulnerability on your business operations, such as data breaches or system outages.
- Urgency: Patches with imminent deadlines or those related to critical business functions should be prioritized.
2. Patch Acquisition:
- Obtaining Patches:
- Vendor Sources: Obtain patches directly from software vendors (e.g., Microsoft, Adobe, Oracle) through their official channels (websites, update servers).
- Third-Party Repositories: Utilize reputable third-party repositories for patches and updates.
- Patch Verification:
- Checksum Verification: Verify the integrity of downloaded patches using checksums to ensure they haven't been tampered with during download.
- Digital Signatures: Check for valid digital signatures from the software vendor to authenticate the authenticity of the patch.
3. Patch Testing:
- Testing Environment: Create a dedicated testing environment (e.g., a test lab) that mirrors your production environment as closely as possible.
- Pilot Deployment: Deploy patches to a small group of test devices or in a non-production environment to identify and address potential issues before widespread deployment.
- Regression Testing: After patch deployment, perform regression testing to ensure that the patch hasn't introduced any unexpected side effects or broken existing functionality.
4. Patch Deployment:
- Automated Deployment: Utilize automated patch management tools to streamline the deployment process across your entire network.
- Scheduled Deployment: Implement schedules for patch deployment to minimize disruption to users and business operations.
- Change Management: Follow proper change management procedures, including documentation and approvals, before deploying any major patches.
5. Patch Reporting and Monitoring:
- Deployment Status: Track the deployment status of patches across all devices and systems in your environment.
- Compliance Reporting: Generate reports on patch compliance levels to identify any gaps in your patch management process.
- Issue Tracking: Monitor for any issues that may arise after patch deployment, such as system instability or unexpected behavior.
6. Continuous Improvement:
- Regular Reviews: Regularly review your patch management process to identify areas for improvement.
- Adjustments: Adjust your policies and procedures based on lessons learned and evolving threat landscapes.
- Staff Training: Provide ongoing training to IT staff on best practices for patch management.
By effectively implementing these key components, organizations can significantly enhance their security posture, improve system stability and minimize the risk of costly cyberattacks
Benefits of Effective Patch Management
- Enhanced Security:
- Vulnerability Mitigation: Patches directly address security vulnerabilities in software, such as those exploited by malware (ransomware, viruses, Trojans), hackers, and other malicious actors. By promptly applying patches, organizations significantly reduce their attack surface and minimize the risk of successful cyberattacks.
- Ransomware Prevention: Many ransomware attacks exploit known vulnerabilities in software. Timely patching can effectively block many ransomware attacks, preventing data encryption and the subsequent demand for ransom payments.
- Improved System Stability: Minimizes system crashes, freezes, and other performance issues.
- Increased Productivity: Reduces downtime and helps maintain business continuity.
- Reduced Costs: Prevents costly data breaches and system failures.
- Improved Compliance: Ensures compliance with industry regulations and security standards.
- Meeting Industry Standards: Many industries have regulations and compliance standards (e.g., HIPAA, PCI DSS, SOX) that require organizations to maintain secure systems. Effective patch management demonstrates compliance with these standards.
- Avoiding Penalties: Non-compliance with these regulations can result in hefty fines and legal repercussions. Patch management helps organizations avoid these penalties.
Challenges of Patch Management
While essential for security and stability, effective patch management presents several significant challenges:
1. Complexity and Scale:
- Diverse Environments: Modern IT environments are increasingly complex, encompassing a wide range of devices (desktops, laptops, servers, mobile devices, IoT), operating systems, and applications. Managing patches across this diverse landscape can be a daunting task.
- Large-Scale Deployments: Deploying patches across thousands of endpoints requires robust infrastructure, automation, and careful planning to avoid disruptions.
2. Resource Constraints:
- Limited IT Staff: Many organizations face resource constraints, with limited IT staff to handle the time-consuming tasks associated with patch management.
- Budget Limitations: Investing in advanced patch management tools and technologies can be costly, presenting budget constraints for some organizations.
3. Patch Testing and Validation:
- Thorough Testing: Thoroughly testing patches in a controlled environment before widespread deployment is crucial to identify and mitigate potential side effects. This process can be time-consuming and resource-intensive.
- Regression Testing: After patch deployment, regression testing is necessary to ensure that the patch hasn't introduced any unexpected issues or broken existing functionality.
4. Downtime and Disruptions:
- Service Interruptions: Patch deployment can sometimes cause temporary service interruptions, impacting user productivity and business operations.
- Unexpected Issues: Even with thorough testing, unexpected issues can arise after patch deployment, requiring immediate attention and remediation.
5. Keeping Up-to-Date:
- Rapidly Evolving Threat Landscape: The threat landscape is constantly evolving, with new vulnerabilities and exploits emerging regularly. Staying informed about the latest threats and ensuring timely patching requires constant vigilance.
- Patch Volume: The sheer volume of patches released by vendors can be overwhelming, making it difficult to keep track of and prioritize critical updates.
6. Managing Third-Party Applications:
- Patch Dependencies: Many organizations rely on third-party applications, and managing patches for these applications can be complex due to dependencies and compatibility issues.
- Vendor Communication: Effective communication with third-party vendors is crucial to obtain timely patch information and address any issues that may arise.
7. Patch Resistance:
- User Resistance: End-users may resist system reboots or other disruptions associated with patch deployment, leading to delays and increased risk.
- Overcoming Resistance: Educating users about the importance of patching and addressing their concerns is crucial to overcome resistance and ensure timely compliance.
8. Remote and Hybrid Workforces:
- Managing Remote Devices: Managing patches for remote devices and endpoints outside the traditional network perimeter presents unique challenges.
- Maintaining Visibility: Ensuring visibility and control over devices in a hybrid work environment is critical for effective patch management.
9. Compliance and Regulations:
- Meeting Industry Standards: Meeting industry regulations and compliance standards (e.g., HIPAA, PCI DSS) often requires specific patch management procedures and documentation.
- Demonstrating Compliance: Demonstrating compliance with these regulations can be challenging, requiring thorough record-keeping and auditing of patch management activities.
10. Emerging Threats:
- Zero-Day Exploits: Zero-day exploits are vulnerabilities that are unknown to the vendor and have no available patch. Responding effectively to these threats requires proactive threat intelligence and rapid response capabilities.
- Supply Chain Attacks: Supply chain attacks target software development and distribution processes, compromising the integrity of software updates. Mitigating these attacks requires robust supply chain security measures.
By acknowledging and addressing these challenges, organizations can develop and implement effective patch management strategies that minimize risk and ensure the security and stability of their IT infrastructure.
Tools for Patch Management
Patch management tools are designed to integrate seamlessly with common operating systems, tracking assets to identify and address missing patches. These tools can apply updates automatically in real-time or according to a predefined schedule. To conserve bandwidth, many solutions first download patches to a central server before distributing them across the network. Advanced tools may also include features for automating patch testing, generating documentation, and rolling back changes if an update causes issues.
Patch management capabilities can be offered as standalone solutions or as part of comprehensive cybersecurity platforms. Many vulnerability management and attack surface management tools include patch management features. Similarly, endpoint detection and response (EDR) tools and unified endpoint management (UEM) platforms often incorporate these functionalities.
By automating patch monitoring, approval, and deployment, these tools significantly reduce manual effort, ensuring timely and efficient application of critical updates.
Explore this article to discover the top patch management software options.
Key Resources for Patch Management
Patch management is a cornerstone of cybersecurity, requiring a structured approach to identify, evaluate, and apply updates to software and systems. To implement an effective patch management strategy, IT administrators can rely on a wealth of external resources and industry standards. These resources offer guidance, updates, and tools to ensure systems remain secure and compliant.
General Cybersecurity and IT Resources
- NIST Cybersecurity Framework: A comprehensive guide to building robust cybersecurity strategies, including patch management best practices.
- CISA Patch Management Practices: Insights and recommendations for maintaining updated systems to protect against vulnerabilities.
- OWASP Top 10: A valuable resource for understanding and mitigating common security risks, complementing patch management efforts.
Vendor-Specific Patch Updates
- Microsoft Security Updates and Microsoft Security Blog: Regular updates, including the widely known Patch Tuesday, to secure Windows systems.
- Ubuntu Security Notices and Red Hat Security Updates: Critical updates for Linux-based systems to address kernel vulnerabilities.
- Apple Security Updates: Patches for macOS and iOS to maintain system integrity.
Final Thoughts
Effective patch management is a critical component of any robust cybersecurity strategy. By proactively identifying, testing, and deploying software updates, organizations can significantly reduce their exposure to cyber threats, improve system stability, and maintain business continuity.
Related Articles:
Frequently asked questions:
-
What is the most critical aspect of patch management?
The most critical aspect of patch management is prioritization. Not all patches are equally important. Prioritizing security patches that address critical vulnerabilities and actively exploited exploits is crucial to minimize the risk of cyberattacks.
-
Why is patch testing important?
Patch testing is crucial for identifying and mitigating potential side effects, such as system instability, application compatibility issues, or performance degradation. Additionally, thorough testing ensures that the patch effectively addresses the intended vulnerability and does not inadvertently introduce new security weaknesses.
-
What are the key challenges of deploying patches?
Key challenges in patch management include potential downtime during deployment, which can disrupt user productivity and business operations. Thoroughly testing and validating patches in a controlled environment can be time-consuming and resource-intensive. Furthermore, staying informed about the latest vulnerabilities and patches requires constant vigilance due to the rapidly evolving threat landscape.
-
How does patch management contribute to business continuity?
By minimizing system downtime, improving system stability, and preventing data breaches, effective patch management helps ensure business continuity. It prevents disruptions to critical business operations and maintains productivity.
-
What are the benefits of using automated patch management tools?
Automated tools streamline the patch deployment process by reducing manual effort and improving efficiency. They also improve consistency and accuracy by minimizing human error in the patch deployment process. Furthermore, automated tools enhance visibility and reporting, providing better insights into patch compliance and deployment status.
-
How does patch management help with regulatory compliance?
Many industries have regulations (e.g., HIPAA, PCI DSS) that require organizations to maintain secure systems. Effective patch management demonstrates compliance with these regulations by ensuring that systems are updated with the latest security patches.
-
What is the role of vulnerability scanning in patch management?
Vulnerability scanning is a crucial first step in patch management. It helps identify existing vulnerabilities in systems and software, allowing organizations to prioritize patches for the most critical issues.