Instantly wake up offline computers and device groups from anywhere with Zecurit's powerful Wake-on-LAN feature
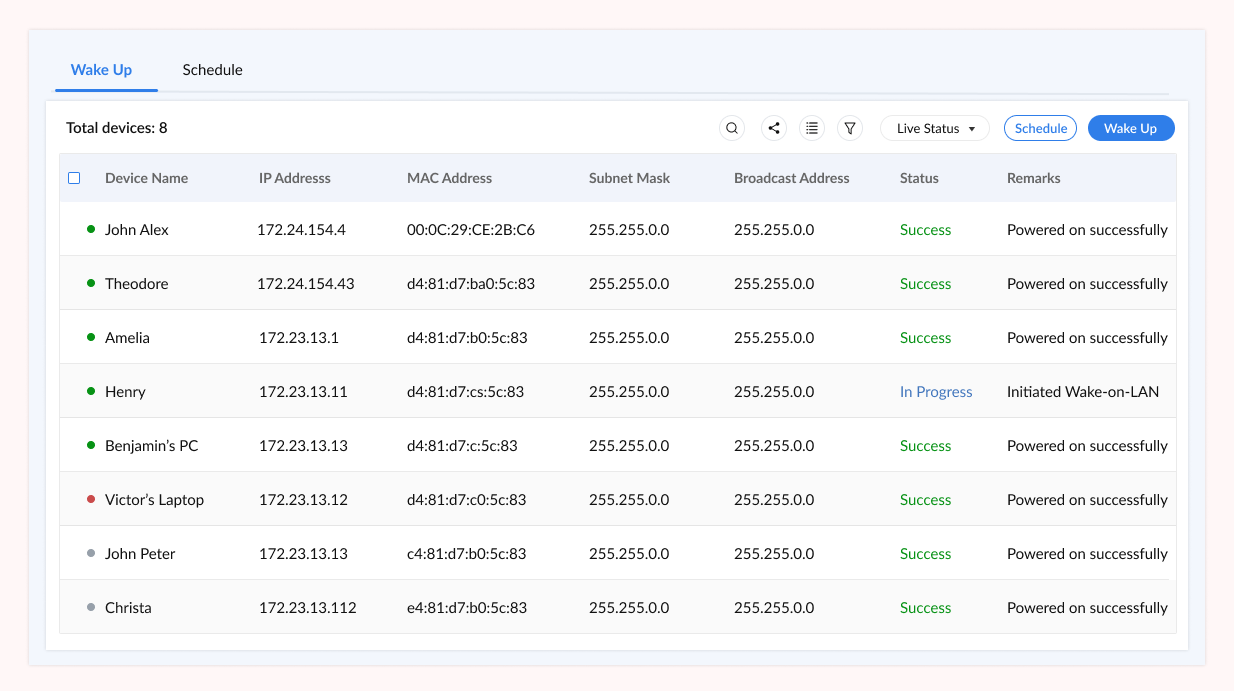
Zecurit Remote Access provides a powerful Wake on LAN (WoL) feature, allowing IT teams to remotely power on offline computers whether individually, in bulk or on a scheduled basis.
Boost productivity, reduce downtime, eliminate unnecessary site visits and maintain complete remote control over your IT infrastructure.
Zecurit’s Wake-on-LAN functionality works through agents installed on managed devices and a secure relay mechanism for distributed networks. The system sends secure magic packets using each device’s MAC and IP address to initiate startup, all managed via a Zecurit console with no need for VPN or physical access.
Streamline IT operations, empower your remote workforce, and keep your endpoints accessible 24/7. With Zecurit’s secure Wake-on-LAN feature, managing offline devices is just a click away.
Contact us today to learn more or book a live demo of Zecurit’s powerful Wake-on-LAN and remote access capabilities.
Wake-on-LAN (WoL) is a network protocol that allows administrators to remotely power on offline computers by sending a "magic packet" to the device's MAC address. In Zecurit Remote Access, WoL is enabled through agents installed on managed devices and relay mechanisms for distributed networks. You can wake devices individually, in bulk, or on a set schedule , all from a centralized cloud dashboard.
Absolutely. Zecurit supports cross-network and remote Wake-on-LAN using secure relay agents. Whether devices are in the same LAN, a remote office, or a different VLAN, Zecurit ensures that wake packets are delivered effectively and securely.
Yes. With Zecurit’s scheduled Wake-on-LAN, you can create automated wake-up routines for individual devices or entire groups. This ensures systems are powered on in time for patches, backups, scans, or remote work access, without manual intervention.
Yes. Zecurit logs every Wake-on-LAN event with detailed audit trails, including timestamps, initiating user, and target devices. All actions are securely transmitted, ensuring compliance, transparency, and accountability for IT teams.
FEATURES
SOLUTIONS
EXPLORE REMOTE ACCESS